Share
Salesforce customer data breaches are surging across every industry. Major corporations including Google, Cisco, Pandora, and Coca-Cola have all fallen victim to coordinated attacks through their Salesforce environments, resulting in millions of compromised customer records. Organizations are scrambling to understand how these attacks succeeded despite sophisticated security measures.
As a Salesforce security expert and the lead software developer at EzProtect, in this blog I am going to explain how attackers are bypassing traditional security controls and why this threat vector is more dangerous than ever.
Most security teams understand perimeter defenses but don’t realize that standard file upload policies and user training cannot protect against sophisticated file-based attacks. While security teams focus on network monitoring and access controls, there’s another entry point that most organizations never consider: unscanned file uploads.
This attack vector remains completely unprotected in most Salesforce environments, creating a pathway that sophisticated attackers are systematically exploiting. Read on to learn how this attack can occur, how EzProtect’s architecture works, and what you can do better protect your company’s most important asset- your company’s data – from cyber-attacks.
The Real-World Impact: When Legitimate Business Processes Become Attack Vectors
Let’s get into a not so hypothetical situation.
Chase, a loan officer at a regional bank, approves a small business loan application and uploads the documentation to their Financial Services Cloud environment for processing and compliance.
A few days later, a colleague needs to review the documentation for a compliance audit. She downloads the business plan document from Salesforce and opens it on her workstation. Suddenly, an alert flashes across her screen: “Your files have been encrypted. Send Bitcoin to this address for decryption key.” Every file on her computer becomes inaccessible, and the ransomware begins spreading through the network.
Salesforce doesn’t scan uploaded files for viruses and without virus scanning capabilities, malicious files infiltrate your Salesforce environment and expose your entire org. This scenario shows how critical it is to not only understand every cyber threat, but also the importance of having Salesforce domain expertise on your IT teams who really understand Salesforce architecture, vendors, and security.
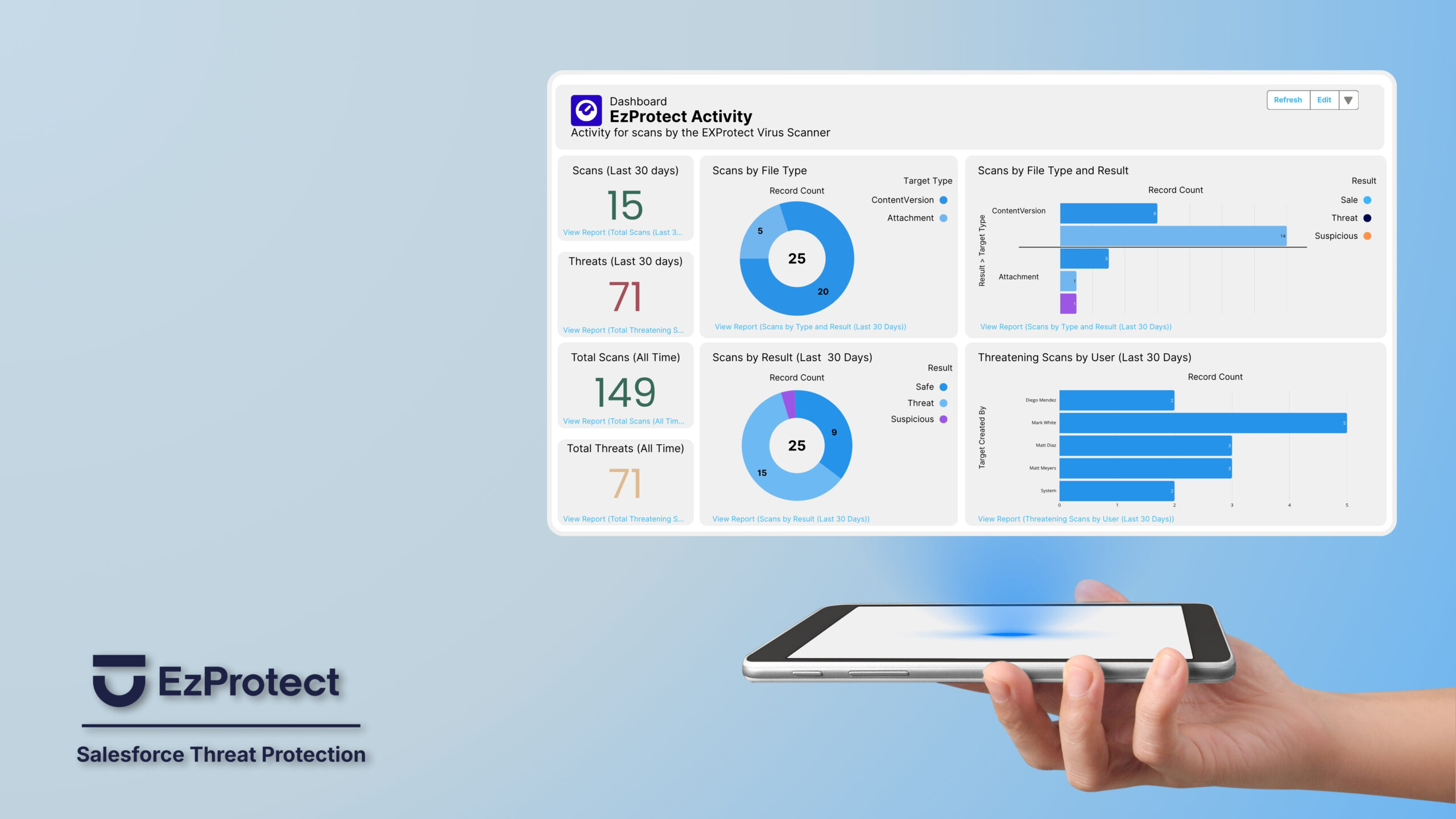
I get asked a lot what is EzProtect and how does it help protect company’s data? Let’s keep it simple to start. Built specifically for Salesforce environments including Experience Cloud, Financial Services Cloud, and Health Cloud, EzProtect delivers real-time, AI-powered virus scanning that detects and blocks malware, phishing, and ransomware attacks before they infiltrate your environment. But in this blog I aim to go deeper and break down how these attacks occur and what you can do to prevent and contain in your orgs. Let’s get into it. 
Salesforce’s File Security Gap
The most dangerous misconception in Salesforce security is assuming the platform protects against file-based threats. The platform does not provide a scanning solution for uploaded files, which creates a massive vulnerability that extends across the entire Salesforce ecosystem.
When users upload files through standard uploads, email-to-case functionality, Experience Cloud sites, or any file storage mechanism, these files bypass all traditional security scanning and enter your environment completely unverified.
The scope of this exposure is broader than most organizations realize. For Experience Cloud sites, administrators might configure file type restrictions to only allow PDFs, images, or documents. However, attackers only need to change the file extension of their malicious content. Salesforce will recognize the fake extension and treat a dangerous executable file as a harmless PDF.
What makes this particularly dangerous is that Salesforce provides file type filtering based on extensions and MIME types—the same methods that skilled attackers easily manipulate. While these controls stop legitimate users from accidentally uploading restricted file types, our security assessments consistently reveal they provide zero protection against malicious actors who understand how to disguise high-risk files as innocent documents.
Why Generic Security Solutions Fail in Salesforce Environments
Unlike network-based or endpoint security tools, Salesforce file security requires understanding the platform’s unique architecture and file handling mechanisms. Generic security solutions typically scan files after they’ve been stored and made accessible to users, creating a dangerous exposure window where malicious content can be executed before detection occurs.
Most enterprise security tools also rely on signature-based detection that sophisticated attackers easily bypass through polymorphic malware, zero-day exploits, and advanced evasion techniques. These solutions cannot provide the real-time, content-based analysis required to protect against the file-based attack vectors that target Salesforce environments.
Business Impact and Beyond Financial Loss
File-based attacks represent a particularly insidious threat because malicious content appears legitimate to users and systems alike. Malicious files uploaded to Salesforce can contain embedded malware, harmful URLs, or executable code disguised as innocent documents. Once inside your Salesforce environment, these threats can spread through your organization via email attachments, shared documents, or automated workflows.
The regulatory implications compound these risks. For organizations in healthcare, financial services, or government sectors, unscanned files containing malware can trigger compliance violations, regulatory fines, and mandatory breach notifications that permanently damage customer trust and industry standing.
Recent breach notifications show average remediation costs exceeding regulatory fines by 300%, as organizations must invest in forensic analysis, system rebuilding, and customer notification processes. Here’s a tool that you can use after this blog to calculate the fiscal impact of what a cyber-attack would have on your organization here.
The Hidden Attack Vector: High-Risk File Types in Business Context
Understanding how attackers exploit unscanned file uploads requires recognizing that cybercriminals specifically choose file types that can execute malicious code while appearing completely legitimate in business contexts.
Executable files like .exe, .bat, and .jar files can run programs directly on user devices, making them perfect vehicles for malware distribution. However, attackers more commonly use document files with macros such as .docm and .xlsm because these appear as legitimate business documents while containing embedded code that can infect systems or steal credentials.
Even seemingly innocent file types pose significant risks. Archive files like .zip and .rar can contain compressed malware or other high-risk file types that decompress after upload. PDF files can embed malicious scripts or links that redirect users to credential-harvesting websites. HTML files can contain dangerous scripts that execute when viewed or redirect users to phishing sites. Get a more detailed breakdown about high-risk files and how to block them in another one of our other popular security resources.
EzProtect’s Advanced Multi-Layered Security Architecture
Recently a customer was switching from another, non-Salesforce security solution to EzProtect and in our initial scan, we found 298 active viruses in a customer’s production environment that their previous enterprise security solution completely missed. These weren’t theoretical threats—they were malicious files accessible to users and capable of causing significant damage. This discovery illustrates why specialized Salesforce file security requires more than generic scanning approaches. But let’s get deeper into actual vulnerabilities that traditional security solutions miss when performing file-scanning. 
Real-Time Upload Quarantine: Eliminating the Exposure Window
The critical vulnerability in most file security approaches occurs during the upload process itself. Traditional security tools scan files after storage and user accessibility, creating a dangerous exposure window. Our approach fundamentally changes this dynamic by implementing immediate quarantine protocols that prevent any access to unverified content.
Our platform immediately blocks every uploaded file by default until our comprehensive scanning process completes. Even during the seconds required for our multi-layer analysis, files remain completely inaccessible to users. This proactive blocking ensures that no user can access unverified content, eliminating the risk window that puts organizations at risk.
Our real-time protection integrates seamlessly with Salesforce’s native upload processes while maintaining full performance standards. The solution utilizes Salesforce’s bulk APIs and batch processes to handle enterprise data volumes without impacting system performance. Our engineering team has specifically optimized these processes to ensure that our security scanning scales faster than Salesforce itself, so the only limitations customers encounter are Salesforce platform limits rather than security processing constraints.
Advanced File Content Analysis: Seeing Through Sophisticated Disguises
The foundation of effective file security begins with accurately identifying file content regardless of extensions or metadata that attackers routinely manipulate. Generic security solutions rely on file extensions and MIME types that can be easily changed, creating a fundamental vulnerability that sophisticated threats routinely exploit.
Our solution employs three distinct scanning methodologies for every uploaded file. The first scanner performs true file type detection by examining the binary structure and content signatures of each file. This deep content analysis examines the actual file headers and binary patterns that define file types at the most fundamental level, determining the true nature of every uploaded file regardless of its extension or metadata.
This content-based detection prevents the most common bypass technique used by attackers—simply changing file extensions to disguise malicious content. While basic security tools can be fooled by renamed extensions, our binary analysis cannot be circumvented by surface-level manipulation because it examines the fundamental structure that defines what a file actually contains.
Our architectural solution approach to this challenge involves examining file signatures at the byte level, identifying specific patterns that correspond to known file types, and detecting discrepancies between claimed file types and actual content. This resource-intensive process provides the highest level of accuracy and resistance to evasion by malicious actors.
Comprehensive Threat Vector Analysis: Multi-Point Security Scanning
Once files are properly identified and their disguises removed, our platform employs comprehensive scanning methodologies that far exceed traditional single-point security approaches. This multi-layered detection ensures that even the most sophisticated attacks cannot evade identification through any attack vector.
The second scanning layer focuses on embedded URL threats that attackers often hide within seemingly innocent files. Our solution analyzes all text content within files, identifying URLs and cross-referencing them against real-time threat intelligence databases that update continuously as new malicious domains are identified globally.
Our URL scanning capability integrates with multiple threat intelligence feeds that update continuously as new malicious domains and URLs are identified worldwide. This ensures that even URLs that became malicious after a file was created will be detected and blocked before users can access potentially harmful content. This protection is particularly critical for PDF documents, Office files, and other formats that commonly contain embedded links.
The third layer employs signature-based virus detection that identifies known malicious patterns using enterprise-grade scanning engines. Our virus scanning utilizes multiple detection engines simultaneously to ensure comprehensive coverage against known threats while maintaining high reliability and low false-positive rates.
AI-Powered Behavioral Analysis: Detecting Zero-Day Threats
The most sophisticated threats require the most advanced detection methods. Our behavioral analysis capability represents the cutting edge of threat detection technology, identifying malicious behavior that static scanning cannot detect—including zero-day threats that have never been seen before.
For files that may contain executable content or suspicious characteristics, our solution performs dynamic analysis in completely isolated sandbox environments. These controlled environments execute files while monitoring their behavior using AI algorithms trained on millions of file execution patterns to identify subtle behavioral indicators that suggest malicious intent.
This behavioral analysis capability allows our platform to detect zero-day threats, polymorphic malware, and sophisticated attacks that have never been seen before, providing protection against the most advanced attack techniques that bypass traditional security measures. By executing files in isolated environments, our system observes actual malicious behavior rather than relying solely on pattern matching or signature detection.
Our sandbox environment utilizes machine learning models that analyze file execution patterns, system modifications, network communications, and other behavioral indicators to determine threat likelihood. This AI-driven approach enables detection of advanced persistent threats, zero-day exploits, and sophisticated malware that traditional security solutions cannot identify. 
Outbound Email Security: Preventing Accidental Malware Distribution
File security extends beyond internal storage to include all methods of file distribution. One of the most overlooked vulnerabilities in Salesforce environments involves outbound email security, where organizations might inadvertently become vectors for spreading malware to customers, partners, and vendors.
When sending emails outside of Salesforce, files leave your protected environment and may be opened by external recipients who lack the same security protections. Our solution addresses this blind spot by scanning all outbound attachments before they leave your Salesforce environment, preventing the transmission of any files identified as threats.
Our email protection capability blocks the transmission of any emails containing files that our scanning engines have identified as malicious. This protection extends beyond your organization’s security perimeter, ensuring that you don’t inadvertently damage business relationships or face legal liability from distributing malware to external parties.
This protection is particularly critical for organizations that frequently share documents with external parties, such as financial institutions sharing loan documents, healthcare organizations transmitting patient records, or government agencies distributing sensitive information. The reputational and legal implications of accidentally sending infected files to external parties can be devastating to business relationships and regulatory compliance.
Legacy System Security: Addressing Historical Vulnerabilities
Many established Salesforce organizations unknowingly harbor significant security vulnerabilities in their legacy data structures. These older file storage methods create unmanageable security risks that most security teams don’t realize exist—perfect repositories for malicious files that may have been lurking undetected for years.
Legacy objects such as attachment objects and document objects follow standard Salesforce permission models, but they lack the advanced security controls available in modern content versions. While users need appropriate profile permissions to access these objects, the critical difference lies in quarantine capabilities. When threats are identified in legacy attachments or documents, Salesforce provides no mechanism to block access to these specific files without removing object-level permissions entirely.
The security implications are severe: once a user has profile access to attachment or document objects, they can download any file stored in these legacy formats, and even if malicious content is detected, no granular quarantine mechanism exists to isolate specific threatening files while preserving access to legitimate content.
We provide comprehensive scanning of all legacy files to identify any historical threats that may have been dormant in your system for years, ensuring that your transition to modern file storage doesn’t inadvertently preserve hidden security vulnerabilities while gaining the ability to quarantine specific threats without disrupting business operations.

Protecting Your Company’s Most Valuable Asset – Your Data
As Salesforce customer data breaches continue to rise, traditional security approaches prove insufficient for protecting modern cloud environments. The hidden vulnerability of unscanned file uploads represents a critical gap that organizations can no longer afford to ignore—a digital gateway that attackers are already exploiting.
File-based attacks will only become more sophisticated as attackers recognize that most organizations leave this attack vector completely unprotected. The time to address this vulnerability is now—before it becomes the pathway that allows cybercriminals to access your most valuable business data.
Organizations that proactively address file security today will be the ones that avoid becoming tomorrow’s breach headlines. The question isn’t whether file-based attacks will target your Salesforce environment—it’s whether you’ll be prepared when they arrive.
Are you actively exposing your data to cyber-attacks? Get a comprehensive Salesforce security assessment from our Salesforce security experts.
About Author:
Nicolás Vásquez is a Lead Software Engineer at EzProtect with over 5 years of specialized Salesforce development experience, currently leading both Salesforce and JavaScript development teams while architecting enterprise-scale solutions. He holds 13 Salesforce certifications including Salesforce Application Architect and Data Architecture and Management Designer, along with specialized expertise in Sales Cloud, Nonprofit Cloud, and Education Cloud implementations. With his dual engineering background in Systems/Computing and Industrial Engineering from Universidad de Los Andes, plus AWS Cloud Practitioner certification, Nicolás brings a comprehensive technical perspective to complex Salesforce platform architecture and data security challenges.
Share
Did you love this blog and wish there could be more?
It is our goal to keep you informed about everything you need to know about Salesforce security to keep your Salesforce data and company safe and secure by providing you with the highest quality of original content.
If this sounds good to you, then sign-up below to be one of the first to know when the next super awesome Salesforce security blog has been released.