Share
Low-code solutions like Flow offer an accessible way to create functionality for guest users, but they come with their own security considerations. These solutions can sometimes make it too easy to run processes in a system context, bypassing normal security checks.
This Salesforce security resource will cover the security implications of using low-code solutions versus custom Apex code for guest user flows in Salesforce Digital Experiences. In addition, this blog will explore the pros and cons of each approach and introduce a hybrid model that balances ease of use with advanced security measures.
The Pros and Cons for Guest User Flows in Low-Code
When using flows for guest users, Salesforce leaders must be extremely cautious about the data being accessed and the actions being performed. It’s crucial to note that Salesforce doesn’t automatically scan uploaded files for viruses, so if guest users have permission to upload files, it could lead to malware infections and potentially allow bad actors to steal your org data.
Always consider how inputs could be manipulated and what unintended consequences might result. Low-code solutions can be secure, but they require the same level of scrutiny and testing as custom code. Be particularly careful with dynamic SOQL in flows, as this can lead to injection vulnerabilities if not properly sanitized and implement additional security measures for file uploads to mitigate the risk of virus infections and data theft.
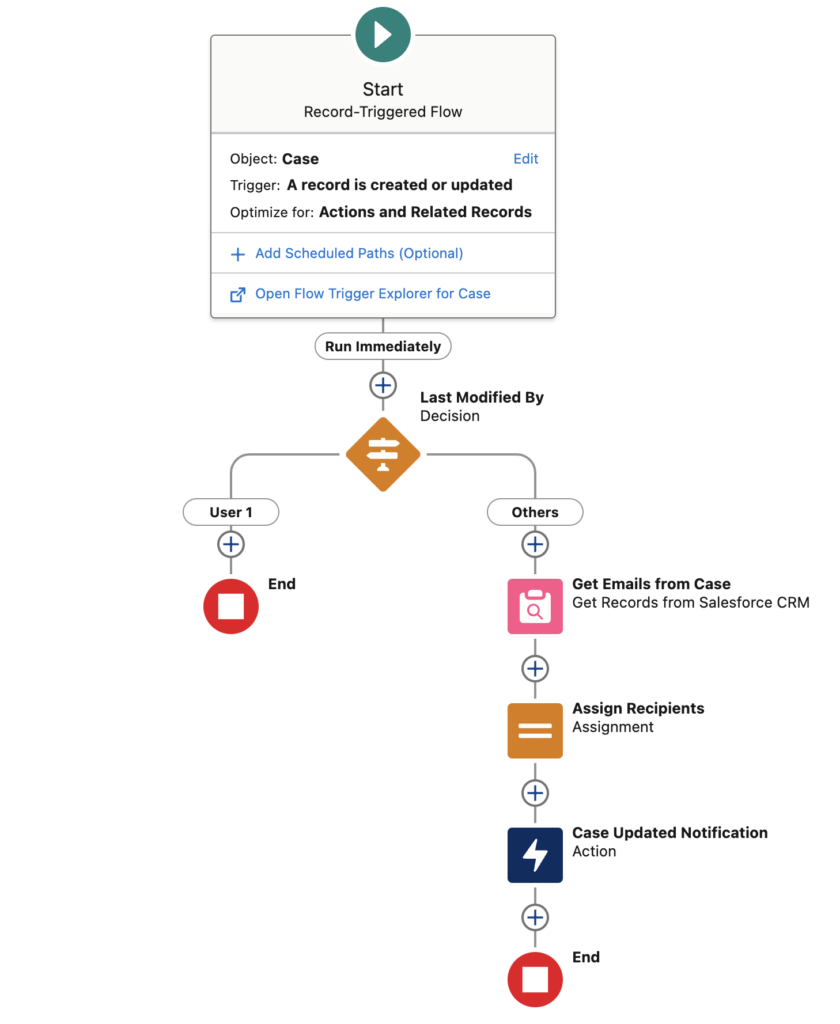
Pro-tip: When using low-code solutions like Flow for guest users, treat them with the same security rigor as custom code. Always validate inputs, minimize system-mode operations, and avoid dynamic SOQL to prevent injection vulnerabilities.
Maximizing Control and Security for Code-Based Approaches
Custom Apex code provides the highest level of control over security in guest user scenarios. When writing Apex for guest user contexts, always use the “with sharing” keyword unless there’s a compelling reason not to.
You will want to separate your Apex classes by security context rather than by business function. This separation helps prevent unintended exposure of sensitive methods to guest users. Implement thorough permission checking in your code, not relying solely on object and field-level permissions.
When it comes to apex classes, always be cautious with ones marked as @AuraEnabled, as these can potentially be executed by guest users through the Lightning framework. Always validate and sanitize inputs and be wary of methods that perform DML operations without proper checks.
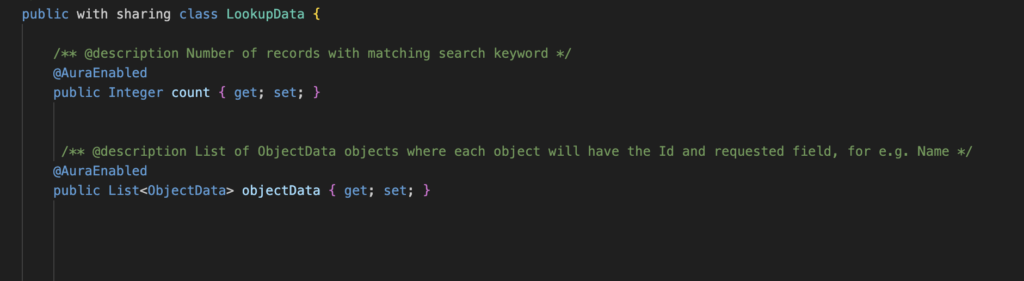
Pro-tip: When writing Apex for guest user contexts, separate classes by security context rather than business function. Use “with sharing” by default, implement thorough permission checks, and be cautious with @AuraEnabled methods that guest users might access.
Combining Low-Code and Code for Optimal Security
A hybrid approach, combining low-code solutions with custom code, can offer a balance of ease of use and security for your org. For example, you might use a flow for the main guest user interaction, but call Apex methods for sensitive operations or data access.
This approach allows you to implement stronger security checks in Apex, while keeping the overall process manageable in a low-code environment. When using this hybrid model, clearly define the boundaries between what the flow handles and what’s delegated to Apex.
For Salesforce leaders balancing both usability and security, use Apex to perform data validation, complex permission checks, and any operations that require elevated system permissions. This separation of concerns can help prevent security oversights, while still leveraging the benefits of low-code development.

Pro-tip: Consider a hybrid approach by using flows for main guest user interactions and Apex for sensitive operations. Clearly define boundaries between flow and Apex responsibilities, using Apex for complex security checks and operations requiring elevated permissions.
Conclusion:
The choice between low-code and code-based solutions for guest user flows isn’t simply about development efficiency; it’s a decision that profoundly impacts security. Remember that just because you can doesn’t mean you should. This applies equally to both low-code and custom-code solutions.
Whether using flows or Apex, the key is to approach development with a security-first mindset. Always consider the potential for misuse or manipulation, especially in guest-user contexts.
By understanding the strengths and weaknesses of each approach and potentially combining them in a hybrid model, organizations can create secure, efficient solutions that meet their business needs while protecting sensitive data and maintaining the integrity of their Salesforce org.
Ready to strengthen your Digital Experience security? Get a free expert assessment without sharing org access. Our experts will help safeguard your Salesforce environment.
Share
Did you love this blog and wish there could be more?
It is our goal to keep you informed about everything you need to know about Salesforce security to keep your Salesforce data and company safe and secure by providing you with the highest quality of original content.
If this sounds good to you, then sign-up below to be one of the first to know when the next super awesome Salesforce security blog has been released.



